Architectures for secure networks
Dual- or Multi-zone Architectures
In most cases, the perimeter defense works on the assumption that what is “good” is inside, and what's outside should be kept outside if possible.
There are two counterexamples:
- Access to resources from remote (i.e., to a web server, to FTP, mail transfer).
- Access from remote users to the corporate network.
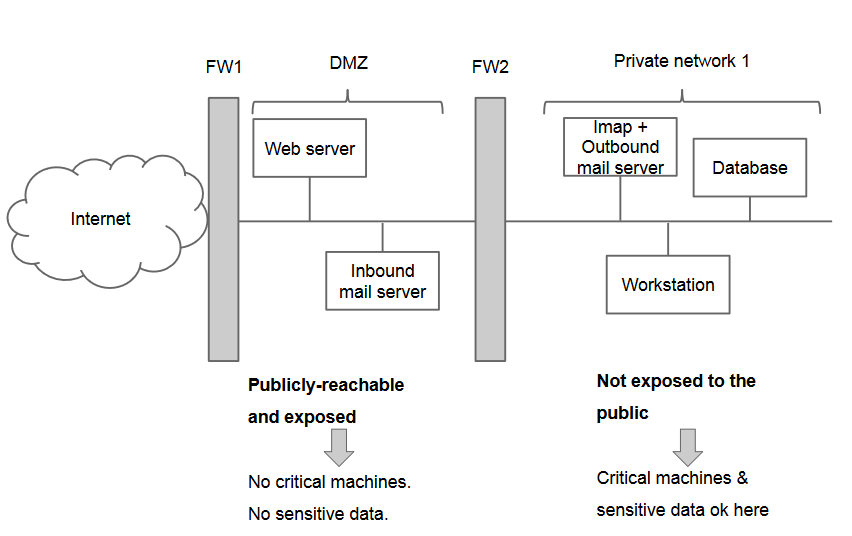
Problem: if we mix externally accessible servers with internal clients, we lower the security of the internal network.
Solution: we allow external access to the accessible servers, but not to the internal network.
General idea: split the network by privileges levels. Firewalls to regulate access.
In practice, we create a semi-public zone called DMZ (demilitarized zone). The DMZ will host public servers (web, FTP, public DNS server, intake SMTP). On the DMZ no critical or irreplaceable data. The DMZ is almost as risky as the Internet.